Introduction to Internal Controls and Preventing Fraud
- Internal Controls and Preventing Fraud: Represent the most critical defense against escalating fraud threats that now affect three out of four organizations across all industries. KPMG Fraud Survey data reveals a disturbing reality—fraud incidents have reached unprecedented levels, creating devastating financial consequences that extend far beyond the initial theft amounts.
- Three-Layered Defense Framework: Preventive controls stop fraud before it occurs, detective controls identify suspicious activities during early stages, and corrective controls address issues after detection while preventing recurrence. Organizations implementing these systematic defenses experience dramatically smaller fraud losses and detect fraudulent activities significantly faster than those lacking such safeguards.
- Small Business Vulnerabilities: Small enterprises face disproportionately severe fraud exposure, experiencing higher fraud frequency from 2002 to 2022 compared to larger organizations. Recovery costs consistently exceed the actual amounts stolen through fraudulent activities, making prevention economically essential rather than merely preferable.
- Emerging Fraud Schemes: Fictitious vendor fraud represents a particularly common scheme where employees steal company funds through false vendors and fabricated invoices. Email scams demonstrate the evolving fraud landscape—these attacks increased 111% from 2018 to 2022, resulting in $2.7 billion in losses during 2022 alone.
- Critical Knowledge for Protection: Understanding internal control mechanisms becomes essential for protecting organizational assets, reputation, and stakeholder interests. This systematic approach provides fundamental principles for effective control systems, vulnerability identification methods, and implementation frameworks that align with regulatory requirements and industry best practices.
- Essential Defense Strategy: Organizations that fail to implement robust fraud prevention systems expose themselves to catastrophic financial losses and reputational damage that can permanently affect business operations and market confidence.
Understanding Internal Controls in Fraud Prevention
- Internal Controls: Serve as the foundation of organizational defense against financial threats that can devastate business operations and stakeholder confidence. Asset misappropriation prevention and unusual transaction pattern detection represent core functions within comprehensive fraud prevention strategies.
1. Definition and Purpose of Internal Controls
- Internal Control Systems: Encompass policies, procedures, and mechanisms specifically designed to ensure accurate financial reporting, promote operational efficiency, and prevent fraud. These comprehensive safety systems utilize means and resources adapted to each organization’s specific operational requirements.
- Primary Control Objectives:
- Asset Protection: Safeguarding assets from theft or misappropriation
- Error Prevention: Preventing, detecting, and correcting errors and irregularities
- Operational Excellence: Promoting operational efficiency and cost-effectiveness
- Regulatory Adherence: Ensuring compliance with applicable laws and regulations
- Reporting Integrity: Providing reliable financial and statistical reports for decision-making
- Dynamic Control Framework: Internal controls represent ongoing processes that evolve with organizational growth rather than static checklists. These systems provide reasonable—not absolute—assurance regarding operational effectiveness, reliable reporting, and regulatory compliance.
- Operational Benefits: Well-designed internal control systems enhance operational efficiency by identifying duplicate procedures, unnecessary processes, and systemic weaknesses. This systematic approach streamlines operations while mitigating risks across financial, operational, compliance, and security domains.

2. Role in Fraud Prevention and Detection
- Control Effectiveness Data: The Association of Certified Fraud Examiners (ACFE) establishes a direct correlation between fraud and internal controls—half of all frauds occurred due to inadequate internal controls. Global fraud losses represent an estimated 5% of annual revenues worldwide, translating into trillions of dollars in losses annually.
- Three-Tiered Fraud Combat Strategy:
- Fraud Prevention: Making fraudulent activities harder to commit
- Early Detection: Increasing the likelihood of discovering fraud during initial stages
- Investigation Support: Facilitating easier investigation when fraud occurs
- Proven Results: Research consistently demonstrates that organizations with internal controls experience smaller fraud losses and detect fraudulent activities more quickly than organizations lacking such safeguards. Four specific anti-fraud controls achieve 50% or greater reduction in both fraud losses and fraud duration: robust codes of conduct, strong internal audit departments, management certifications of financial statements, and management reviews of internal controls.
- Deterrent Effect: Proactive anti-fraud controls communicate clear organizational messages to employees, vendors, customers, and other stakeholders about zero tolerance for fraudulent behavior. This enhanced perception of detection risk, combined with making fraud inconvenient and dangerous for potential perpetrators, significantly reduces fraudulent activity likelihood.
3. Connection to Corporate Governance and Ethics Policy
- Governance Integration: Internal controls form essential components of corporate governance mechanisms by serving as practical enforcement tools for organizational moral codes. Robust controls underpin both governance and compliance—without them, corporations cannot effectively monitor and enforce adherence to relevant laws, regulations, and policies.
- Ethical Foundation: Effective internal control systems begin with integrity and ethical values established through “tone at the top” leadership. Research demonstrates that corporate governance, ethical culture, and Internal Controls over Financial Reporting (ICFR) each contribute significantly to regulatory compliance. Boards of directors play crucial roles in defining integrity expectations and internal control responsibilities.
- Regulatory Framework: The Sarbanes-Oxley Act implementation in 2002 mandated internal control over financial reporting for publicly traded companies in the United States. This legislation, enacted following major corporate frauds and money laundering scandals, established new compliance standards designed to protect investors.
- Symbiotic Relationship: The connection between ethics and internal controls operates symbiotically—employees in organizations with high ethical standards demonstrate greater likelihood to adopt and enforce internal controls. Without ethical culture, employees may engage in defiant behaviors that undermine control effectiveness. Organizations must foster cultures that value transparency, accountability, and ethical behavior as foundational elements supporting control systems.
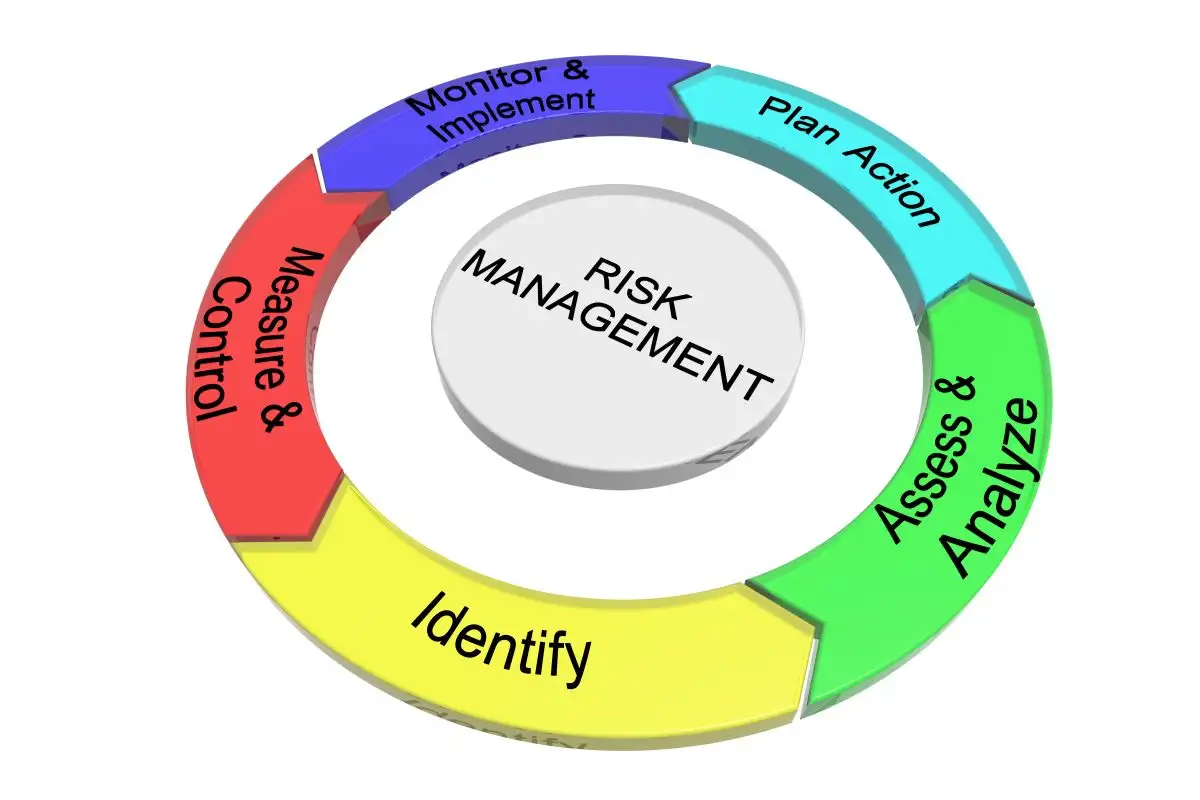
Internal Control Framework: Three Critical Defense Mechanisms
- Comprehensive internal controls framework operates through three interconnected defense mechanisms that create systematic protection against fraudulent activities. Each control type serves distinct functions within organizational security architecture, enabling companies to design targeted anti-fraud programs that address specific vulnerabilities.
Preventive Controls: Eliminating Fraud Opportunities
- Preventive controls function as proactive barriers designed to eliminate fraud opportunities before they materialize. These controls operate as the primary defense line, similar to security systems that deter criminal activity through visible protection measures.
Essential Preventive Control Components:
- Segregation of duties: Prevents single-person control over complete transaction cycles. This fundamental control separates initiating, approving, recording, reconciling transactions, asset handling, and report reviewing functions. Collusion Requirements: This separation makes individual fraud virtually impossible without multiple employee collaboration.
- Access Controls and Authorization: Least privilege principle ensures users receive only essential access rights for their specific job functions. Physical asset controls and IT password restrictions create additional barriers to unauthorized system access.
- Anti-Fraud Policies: Comprehensive policies, codes of conduct, and ethical guidelines must be accessible to all personnel. Organizations with robust codes of conduct experienced 50% or greater reduction in both fraud losses and detection duration.
- Employee Screening and Rotation: Thorough background verification for new hires and systematic job rotation policies prevent long-term exploitation of system vulnerabilities.
- Training and Awareness Programs: Regular anti-fraud education ensures employees understand their fraud prevention responsibilities.
Detective Controls: Early Fraud Identification Systems
- Detective controls identify fraudulent activities after occurrence but before significant damage accumulates. While prevention remains preferable, detective measures provide essential verification that preventive controls function effectively.
Critical Detective Control Elements:
- Regular Audits: Internal audits focus on performance improvement while external audits verify financial statement accuracy. These systematic investigations determine whether fraud exists or develops within business operation
- Account Reconciliations: Monthly reconciliation of detailed account transactions represents one of the most crucial control mechanisms. This process creates systematic checks and balances that detect fraud, theft, inappropriate fund usage, or human errors.
- Transaction Monitoring: Automated systems analyze patterns and flag suspicious activities including large transactions, international purchases, or dormant account activity.
- Exception Reporting: Specialized reports highlight transactions outside normal parameters, enabling early issue identification before escalation.
- Physical Inventory Verification: Regular counts of physical assets and inventory ensure recorded amounts match actual quantities.
Corrective Controls: Post-Incident Response and Prevention
- Corrective controls activate after detective controls identify fraud or irregularities. These measures remedy discovered problems while preventing similar future occurrences.
Key Corrective Control Strategies:
- Disciplinary Actions: Appropriate consequences for fraud perpetrators deter others from similar behavior. Error vs. Fraud: Errors require positive discipline like additional training rather than punitive measures.
- Policy Updates: Systematic revision of existing policies addresses investigation-discovered weaknesses. 82% of victim organizations modified their anti-fraud controls following fraud incidents.
- System Improvements: Software patches and modifications address vulnerabilities that fraudsters exploited.
- Process Reviews: Comprehensive assessments examine fraud causation, process failures, and prevention strategies.
- Continuous Improvement: Ongoing risk assessments address inherent risks while maintaining acceptable residual risk levels, even without fraud occurrence.
- Multi-Layered Strategy Benefits: Effective internal control systems integrate all three control types through balanced approaches. This comprehensive strategy makes fraud commission more difficult, increases early detection likelihood, and ensures appropriate incident responses.
Fraud Risk Assessment: Strategic Vulnerability Identification
- Fraud risk assessments enable organizations to systematically identify, analyze, and prioritize potential vulnerabilities before they escalate into costly incidents. This methodical approach allocates resources toward the most significant threats facing business operations while establishing baseline defenses against evolving fraud schemes.
Identifying Inherent Risks in Business Processes
- Inherent risk represents the raw vulnerability level existing before implementing any controls or safeguards. Business activities carry natural vulnerabilities based on their complexity, volume, or operational nature. Understanding inherent risk provides essential baselines for developing targeted mitigation strategies.
Critical Risk Factors:
- Nature of Business Activities: Operations inherently carry higher fraud risk based on their purpose, scope, and industry characteristics.
- Transaction Complexity and Volume: Complex processes increase inherent risk through greater likelihood of human errors and management oversight failures.
- External Economic Conditions: Market instability and regulatory changes amplify existing vulnerabilities across all business functions.
- Historical Fraud Incidents: Previous occurrences indicate potential systemic weaknesses that may persist without systematic remediation.
- Qualified specialists and subject-matter experts must contribute specialized guidance when employing advanced analysis techniques. This collaborative approach captures potential fraud scenarios across organizational functions while ensuring comprehensive vulnerability identification.
- Effective fraud risk assessment identifies specific tools, methods, and information sources for gathering fraud risk data, including schemes and trends from monitoring activities. Thorough approaches ensure no significant vulnerabilities remain unaddressed during the assessment process.
Risk Assessment Matrix Implementation
- Risk assessment matrices serve as visual tools depicting likelihood and severity of identified fraud risks. These matrices help prioritize threats requiring immediate examination and mitigation. Standard matrices include rows for each risk and columns for risk measures including impact and likelihood.
Effective Risk Matrix Development:
- Impact Assessment: Consider financial and non-financial consequences including reputation damage, regulatory violations, and stakeholder relationship deterioration.
- Likelihood Evaluation: Examine past fraud occurrences, industry fraud prevalence, and process complexity factors.
- Visual Risk Mapping: Plot impact against likelihood to create clear significance indicators for prioritization decisions.
- Heat maps use color coding systems—red for highest priority, orange for significant risks, yellow for manageable concerns—to represent risk levels visually. Heat map limitations include equal weighting of impact and likelihood, whereas impact typically takes precedence in fraud risk evaluation.
Determining Residual Risk Levels
- Residual risk remains after management implements internal controls to reduce and manage identified threats. No internal control program can eliminate all threats completely—some residual risk always persists. The standard calculation formula:
Residual Risk = Inherent Risk – Impact of Mitigation Controls
- Risk Tolerance Alignment: Organizations must determine whether residual risk levels align with defined tolerance thresholds. When residual risk exceeds acceptable levels, consider these strategic options:
- Discontinue risky activities entirely
- Accept risk within tolerance through enhanced monitoring
- Conduct detailed audits or control effectiveness testing
- Implement additional controls to reduce likelihood or impact
- Cost-Benefit Analysis becomes critical—additional control deployment costs may exceed benefits. Controls that create unnecessary administrative burdens can inconvenience employees and customers without proportional risk reduction.
- Regular monitoring of residual risk levels proves essential for maintaining effective control environments. Organizations that increase operational complexity—such as adding bank accounts while maintaining monthly reconciliation schedules—may experience residual risk increases to unacceptable levels.
Preventive Control Design: Strategic Defense Against Fraud
- Preventive controls function as the primary barrier against fraudulent activities, stopping schemes before they can take root within organizational operations. Strategic implementation of structural safeguards and awareness measures creates multiple layers of protection that minimize opportunities for dishonest activities.
Segregation of Duties: The Foundation of Transaction Security
- Segregation of duties (SoD) distributes transaction responsibilities across multiple individuals, making fraud virtually impossible without employee collusion. This fundamental control principle requires systematic separation of key transaction stages to eliminate single-person control over complete processes.
- Critical separation requirements include:
- Initiation: Requesting purchases or payments
Approval: Authorizing transactions
Recording: Entering data into systems
Reconciliation: Verifying accuracy
Asset custody: Physical handling of assets
- Initiation: Requesting purchases or payments
- Research confirms that least two sets of eyes must review any financial transaction. Practical segregation examples demonstrate this principle:
- The person requisitioning purchases cannot approve those same purchases. Cash receipt collectors must differ from deposit handlers. Invoice approval personnel cannot maintain check custody. Accounting record keepers cannot handle physical assets.
- Compensating controls become necessary when organizations lack sufficient personnel for ideal segregation—detailed supervisory reviews provide alternative protection. Regular rotation of key internal control responsibilities strengthens segregation effectiveness.
Access Controls: Implementing Least Privilege Security
- The principle of least privilege grants users only the minimum access required for their specific job functions—nothing more. This approach dramatically reduces security vulnerabilities and limits potential breach impact.
Effective implementation strategies:
- Default user accounts to minimal privileges. Conduct regular privilege audits identifying unused permissions. Replace overly permissive permissions with restricted alternatives. Separate administrator accounts from standard user accounts. Implement just-in-time access elevation for temporary needs. Monitor all privileged account activities.
- Privilege creep represents a significant security threat—the gradual accumulation of unnecessary access rights following role changes. Regular access reviews maintain secure environments throughout organizational personnel transitions.
Employee Training Programs: Building Human Firewalls
- Fraud awareness training delivers substantial protective value. Organizations lacking comprehensive training programs lose nearly twice as much to fraud compared to those implementing systematic staff education. Trained employees generate tips at twice the rate of untrained staff.
- Comprehensive training components:
- Case studies from industry-specific fraud incidents. Interactive exercises identifying fake invoices and ghost employees. Current reporting mechanisms and utilization procedures. Ethical conduct guidelines and organizational policies. Regular refresher courses covering emerging fraud trends.
- Tone at the top principles require leadership participation demonstrating organizational commitment to fraud awareness. Senior management involvement directly influences program effectiveness and workplace ethical standards.
IT Security Infrastructure: Technical Safeguards
- Firewalls control network traffic between systems with different security requirements. Despite evolving threat landscapes, firewalls remain essential for blocking significant lower-layer attacks.
Firewall implementation requirements:
- Create policies specifying traffic handling procedures. Block unauthorized inbound and outbound communications. Develop performance-supporting rulesets. Manage components throughout solution lifecycles. Integrate threat intelligence feeds enhancing detection capabilities. Conduct regular configuration and log audits.
- Additional security measures include robust password policies, encrypted VPN connections, and antivirus protections. Multi-factor authentication strengthens system access by requiring multiple verification methods.
- Integrated system approach: Preventive controls function as interconnected security mechanisms whose effectiveness depends on proper design, implementation, and ongoing maintenance across organizational operations.
Detective Controls: Early Warning Systems Against Fraudulent Activities
- Detective controls represent the critical secondary defense mechanism designed to identify fraudulent activities that breach preventive measures. These systematic monitoring processes provide essential early warning signals that enable organizations to intervene before fraud schemes escalate into catastrophic financial losses.
Physical Inventory Verification: Detecting Asset Misappropriation
- Regular physical inventory counts serve as fundamental detective controls that expose discrepancies between recorded inventory and actual physical assets. Organizations conducting unannounced physical counts of assets, raw materials, and finished goods maintain inventory accuracy while demonstrating management vigilance against theft and misappropriation.
- Verification Methods: Physical inventory verification employs multiple systematic approaches:
- Cycle counts: Regular verification of specific inventory sections throughout operational periods
- Perpetual counts: Ongoing verification processes that maintain continuous inventory monitoring
- Complete “wall to wall” counts: Annual verification covering entire inventory holdings
- Surprise Audit Effectiveness: Unannounced inventory audits conducted during non-standard periods—mid-month, weekends, or early morning hours—prove particularly effective because they prevent fraudsters from manipulating inventory before scheduled counts. Comparison analysis between physical count results and general ledger records reveals potential fraud indicators including unexplained inventory write-offs or suspicious inventory turnover ratios.
Bank and Account Reconciliations: Critical Cash Internal Controls Mechanisms
- Monthly bank reconciliations function as essential detective controls that compare banking records against accounting records to ensure perfect alignment. This systematic verification process identifies unauthorized activities while providing management accurate cash position information.
- Effective Reconciliation Framework:
- Monthly reconciliation requirements mandated under Budgeting, Accounting and Reporting System (BARS) Manual standards
- Four-column reconciliation processes that reconcile both revenues/expenditures and beginning/ending cash balances
- Documentation protocols requiring source documents and detailed comparison schedules
- Investigation procedures for each reconciling item to identify potential fraudulent activities
- Segregation Requirements: Staff responsible for bank reconciliations must remain separate from deposit handling, accounts payable processing, payroll check distribution, or electronic fund transfer authorization. This segregation principle ensures that errors or suspicious activities receive identification from independent personnel rather than those performing original duties.
Audit Trails and Transaction Monitoring: Digital Fraud Detection
- Audit trails create detailed chronological records of all system activities, transactions, and modifications, establishing transparency around user actions and system changes. These comprehensive logs track successful and failed login attempts, program executions, transaction details, and master record modifications.
- Multi-Level Monitoring Systems:
- System-level trails: Monitor IT system performance and security events across organizational infrastructure
- Application-level trails: Track software usage patterns and application-specific changes
- User audit trails: Record individual user actions, commands, and system interactions
- Security audit logs: Capture login attempts and access to sensitive transaction systems
- Fraud Detection Capabilities: Audit trail analysis enables organizations to review access histories, examine security modifications, monitor attempted security breaches, and detect potential fraud through pattern recognition. These detailed records provide crucial evidence during fraud investigations while simultaneously deterring fraudulent behavior through increased detection awareness.
- Early Intervention Strategy: Organizations implementing these detective control systems gain essential visibility into potentially fraudulent activities, enabling intervention before financial losses escalate into organizational crises.
Corrective Controls and Continuous Improvement
- Post-Incident Response: Organizations discovering fraudulent activities face critical decisions that determine whether they strengthen their defenses or remain vulnerable to future attacks. Corrective controls serve as the final line of defense, addressing discovered weaknesses while preventing similar occurrences from devastating organizational operations.
- Swift Decisive Action: Becomes essential once fraud confirmation occurs, as delayed responses signal organizational weakness to potential perpetrators throughout the enterprise.
Disciplinary Actions and Policy Framework Updates
- Disciplinary Measures: Following fraud confirmation, organizations must implement firm disciplinary action that demonstrates the serious consequences of fraudulent behavior . Clear messaging about fraud consequences creates powerful deterrence effects that protect against future incidents.
- Error vs. Fraud Distinction: Cases involving unintentional errors require positive discipline approaches such as additional training rather than punitive measures.
- Effective Disciplinary Framework:
- Documentation Requirements: Clear incident documentation and response protocols that establish consistent organizational standards.
- Severity-Based Consequences: Implementation of proportionate disciplinary measures based on fraud magnitude and intent.
- Whistleblower Protections: Establishing comprehensive safeguards that encourage reporting without fear of retaliation.
- Policy Evolution: Research demonstrates that 82% of victim organizations modified their anti-fraud controls following fraud incidents. Updated policies must address specific weaknesses uncovered during investigations while creating stronger barriers against similar future attempts.
Technology-Based Vulnerability Remediation
- Software Security Patches: Modern fraud schemes increasingly exploit technological vulnerabilities, making software patches and system updates essential components of corrective control frameworks.
- Security patches address specific vulnerabilities within programs or products that fraudsters may exploit.
- Critical Patching Protocols:
- Immediate Installation: Updates must be installed promptly to protect against attackers who exploit known vulnerabilities.
- Trusted Vendor Updates: Automatic updates from verified vendors provide consistent protection without administrative burden.
- Secure Update Channels: Avoiding updates over untrusted networks unless using Virtual Private Network protection.
- Legacy System Retirement: All end-of-life software that no longer receives security updates must be replaced or discontinued.
- Interim Protection Measures: Organizations requiring significant time for system changes should implement temporary manual controls. Manual vendor reviews and independent check run report analysis provide immediate risk mitigation while permanent solutions are developed.
Post-Incident Control Assessment and Enhancement
- Agile Response Requirements: Fraud threats evolve rapidly, demanding organizational agility in response strategies . SMART remediation plans (Specific, Measurable, Achievable, Relevant, Time-based) must detail comprehensive implementation frameworks:
- Responsibility Assignment: Clear identification of personnel accountable for implementing each corrective action.
- Action Specifications: Detailed descriptions of required corrective measures and implementation methods.Timeline Requirements: Specific deadlines for implementation phases and completion milestones.
- Documentation Standards: Comprehensive record-keeping requirements for audit trails and compliance verification.
- Independent Monitoring: Control effectiveness monitoring should be conducted by independent parties such as internal audit departments or third-party consultants . Monitoring processes include periodic follow-ups with assigned personnel, assessment of new control design effectiveness, and operational testing after sufficient implementation periods.
- Strengthened Defense Environment: These corrective measures create increasingly robust internal control environments that make future fraud attempts significantly more difficult while reinforcing organizational cultures of integrity and ethical conduct throughout all operational levels.
Building a Culture of Integrity and Accountability
- Ethical organizational culture forms the critical foundation upon which all internal control systems depend for effective fraud prevention. Sophisticated control mechanisms prove worthless without an organizational environment that values integrity and accountability at every operational level.
Tone at the Top and Leadership Behavior
- Leadership behavior creates the ethical foundation that determines whether fraud prevention measures succeed or fail within organizations. Research demonstrates that ethical tone established by top management produces direct effects on employee conduct throughout the organization. Healthy organizational cultures effectively mitigate and deter unethical behavior, while their absence emboldens employees to act improperly or fail to report misconduct.
- Essential characteristics of positive ethical leadership include:
- Demonstrating ethical behavior consistently across all business dealings • Maintaining complete transparency regarding financial decisions
- Establishing clearly defined Codes of Ethics accessible to all personnel • Exhibiting unwavering commitment to honesty and integrity
- Middle management influence extends beyond C-suite directives. These managers represent the most visible face of leadership to frontline employees. Their daily interactions shape organizational expectations about acceptable behavior patterns. Middle managers must actively challenge fraud rationalizations while encouraging prompt reporting of ethical concerns.
Whistleblower Protection and Reporting Mechanisms
- Effective whistleblowing systems constitute essential components of comprehensive fraud prevention strategies. Organizations must establish safe, independent channels that allow personnel to report concerns without fear of retaliation. Association of Certified Fraud Examiners data reveals that median losses to occupational fraud increased 24% over just two years, demonstrating the critical need for robust reporting infrastructure.
- Functional whistleblowing mechanisms require employee confidence that:
- Concerns receive confidential treatment throughout investigation processes • Reporters face no retaliation for bringing forward legitimate issues
- Reports undergo prompt and transparent investigation procedures
- SEC Whistleblower Program results demonstrate remarkable effectiveness—since 2011, the program has awarded more than $2 billion to whistleblowers while recovering billions in financial penalties from violating organizations.
Sarbanes-Oxley Act Requirements for Internal Controls
- Sarbanes-Oxley Act of 2002 established rigorous accountability standards following devastating corporate scandals including Enron and WorldCom. Section 404(a) mandates management assessment and reporting on internal control effectiveness, while Section 404(b) requires independent auditor attestation of management assessments.
- SOX certification requirements hold executive officers personally responsible for establishing and maintaining adequate internal controls. Principal executives must certify their evaluation of control effectiveness while disclosing any significant deficiencies or material weaknesses to auditors.
- Legislative framework creates direct connections between corporate culture and regulatory compliance, compelling leadership to prioritize ethical conduct throughout their organizations while establishing personal accountability for fraud prevention system effectiveness.
Monitoring, Auditing, and Regulatory Compliance: Essential Oversight for Fraud Prevention
- Continuous monitoring forms the backbone of effective fraud prevention systems, ensuring internal controls maintain their strength against evolving threats. Organizations that fail to implement systematic oversight expose themselves to exploitation by fraudsters who target weakened or outdated control systems.
Internal Audits and Management Reviews: Independent Fraud Detection
- Internal audit functions provide crucial independent verification that controls effectively mitigate fraud risks through systematic evaluation of organizational policies and procedures. Internal audit ranks second only to tips in detecting fraud, demonstrating the vital role these functions play in organizational protection.
- Significant Impact on Fraud Losses: Organizations with strong internal audit departments experience 50% or greater reduction in both fraud losses and duration. This dramatic improvement occurs through several key audit program components:
- Surprise audits performed at non-standard times like weekends or early mornings
- Data analytics for identifying unusual patterns in transactions
- Regular testing of control effectiveness across all operational area
- Detection Superiority: The effectiveness of well-designed audit programs creates multiple checkpoints that make fraudulent activities significantly harder to execute without detection.
Ensuring Compliance with Regulatory Enforcement Standards
- Regulatory compliance monitoring requires continuous assessment of adherence to regulatory requirements, internal policies, and industry standards. Most regulators in the US and UK now mandate some form of compliance monitoring, reflecting the critical importance of systematic oversight programs.
- Regulatory Requirements: The UK Financial Conduct Authority mandates having a compliance monitoring plan before approving financial market companies. This requirement demonstrates how regulatory bodies recognize monitoring as essential for market integrity and investor protection.
- Adaptive Compliance Programs: Effective compliance frameworks must incorporate regular policy updates to reflect changing regulations or business operations. Compliance represents a moving target that requires monitoring programs to remain agile and responsive to evolving requirements.
Securities Fraud Litigation Standards and Control Accountability
- Securities fraud claims frequently challenge organizational statements about regulatory compliance effectiveness. Organizations must carefully consider public disclosures about their compliance programs, as these statements can become the foundation for litigation when control failures occur.
- Management Certifications: Management certifications of financial statements establish direct accountability for control effectiveness. Under the Sarbanes-Oxley Act, executives bear personal responsibility for internal controls effectiveness, creating substantial legal exposure for control deficiencies that enable fraudulent activities.
- Legal Consequences: This regulatory framework ensures that monitoring and auditing failures can trigger both regulatory enforcement actions and private litigation, making robust oversight programs essential for organizational protection.
THE SECURITIES LITIGATION PROCESS
| Filing the Complaint | A lead plaintiff files a lawsuit on behalf of similarly affected shareholders, detailing the allegations against the company. |
| Motion to Dismiss | Defendants typically file a motion to dismiss the securities class action lawsuits, arguing that the complaint lacks sufficient claims. |
| Discovery | If the motion to dismiss in the securities litigation is denied, both parties gather evidence, documents, emails, and witness testimonies. This phase of securities litigation can be extensive. |
| Motion for Class Certification | Plaintiffs request that the court to certify the securities litigation as a class action. The court assesses factors like the number of plaintiffs, commonality of claims, typicality of claims, and the adequacy of the proposed class representation. |
| Summary Judgment and Trial | Once the class is certified, the parties may file motions for summary judgment in the securities litigation. If the case is not settled, it proceeds to trial, which is rare for securities class actions. |
| Settlement Negotiations and Approval | Most securities litigation cases are resolved through settlements, negotiated between the parties, often with the help of a mediator. The court must review and grant preliminary approval of the securities litigation to ensure the settlement is fair, adequate, and reasonable. |
| Class Notice | If the court grants preliminary approval, notice of the settlement is sent to all class members in the securities litigation, often by mail, informing them about the terms and how to file a claim. |
| Final Approval Hearing | The court conducts a final hearing to review any objections and grant final approval of the settlement of the securities litigation. |
| Claims Administration and Distribution | A court-appointed claims administrator manages the process of sending notices in the processing claims from eligible class members, and distributing the settlement funds. The distribution is typically on a pro-rata basis based on recognized losses. |
Essential Defense Against Organizational Destruction
- Internal control systems represent the fundamental barrier between organizational survival and catastrophic fraud-related collapse. Multi-layered defense strategies combining preventive internal controls, detective internal controls, and corrective internal controls create essential protection against fraudulent activities that can destroy business operations and stakeholder confidence along with robust corporate governance.
- Financial Reality: Recovery costs consistently exceed stolen amounts, making fraud prevention an economic imperative rather than a discretionary expense. Organizations that treat internal controls as investments rather than administrative burdens position themselves for sustainable operations and market credibility.
- Four Critical Foundation Elements:
- Segregation of duties prevents single-person transaction control and eliminates fraud opportunities
- Regular risk assessments identify vulnerabilities before exploitation occurs
- Comprehensive policy documentation establishes clear operational standards and accountability measures
- Strong ethical culture led through management example creates organizational integrity expectations
- Integrated Defense Architecture: Detective internal controls including surprise audits and account reconciliations identify fraud attempts that bypass preventive measures. Corrective controls ensure continuous system strengthening after incident discovery and response.
- Cultural Foundation: Internal controls effectiveness depends fundamentally on organizational culture. Management must demonstrate personal commitment to ethical conduct while establishing clear behavioral expectations. Whistleblower protections and anonymous reporting channels encourage early fraud detection and intervention.
- Regulatory Framework: Sarbanes-Oxley Act provisions provide structured guidance for public companies, though all organizations benefit from adopting similar accountability principles. Regular monitoring ensures controls remain effective against evolving fraud tactics while demonstrating stakeholder commitment.
- Organizational Vigilance: Fraud prevention requires sustained attention across all organizational levels as part of strong internal controls . Anti-fraud programs that integrate technological safeguards with human awareness create environments where fraudulent activities become increasingly difficult to execute and conceal.
- Protection Strategy: Organizations implementing these systematic strategies significantly reduce fraud risk with robust internal controls while protecting assets, reputation, and stakeholder trust. Truth emerges that proactive defense measures cost substantially less than post-fraud recovery efforts and reputational rehabilitation.
Key Takeaways
Organizations face escalating fraud threats, with three out of four companies reporting fraud incidents and recovery costs typically exceeding the stolen amounts. This comprehensive guide reveals how strategic internal controls and strong corporate governance can transform your organization’s defense against financial crimes.
• Implement three-layered defense: Combine preventive controls (segregation of duties, access restrictions), detective controls (audits, reconciliations), and corrective controls (policy updates, disciplinary actions) for comprehensive fraud protection.
• Conduct regular fraud risk assessments as part of internal controls : Use risk matrices to identify inherent vulnerabilities in business processes, then implement targeted controls to reduce residual risk to acceptable levels.
• Establish strong ethical culture as part of internal controls: Leadership must demonstrate integrity through actions, not just words—organizations with robust codes of conduct experience 50% greater reduction in fraud losses and detection time.
• Segregate duties across all transactions: Ensure no single person controls initiation, approval, recording, and reconciliation of financial transactions to prevent fraud without collusion.
• Monitor continuously through audits: Organizations with strong internal audit departments detect fraud faster and lose significantly less money compared to those lacking systematic oversight programs.
The most effective anti-fraud programs combine technological safeguards with human awareness, creating environments where fraudulent activities become increasingly difficult to execute while protecting organizational assets and stakeholder trust.
FAQs
Q1. What are the three main types of internal controls for fraud prevention? The three main types of internal controls are preventive controls (to stop fraud before it occurs), detective controls (to identify fraud early), and corrective controls (to respond to fraud incidents and prevent recurrence).
Q2. How does segregation of duties in internal controls help prevent fraud? Segregation of duties in your internal controls prevents fraud by ensuring no single person controls an entire transaction from start to finish. This makes it much more difficult for an individual to commit fraud without collusion.
Q3. Why is conducting regular fraud risk assessments important for internal controls? Regular fraud risk assessments are crucial for identifying vulnerabilities in business processes, prioritizing threats, and allocating resources effectively to mitigate the most significant risks facing an organization.
Q4. What role does organizational culture play in fraud prevention in internal controls? Organizational culture is fundamental to fraud prevention. A strong ethical culture, led by management example, creates an environment where fraudulent activities are less likely to occur and more likely to be reported.
Q5. How effective are whistleblower programs in detecting fraud? Whistleblower programs are highly effective in detecting fraud. Tips, often from employees, are the most common method of fraud detection. Organizations with robust whistleblower policies typically experience smaller fraud losses and detect fraud more quickly.
Contact Timothy L. Miles Today for a Free Case Evaluation About Securities Class Action Lawsuits
If you suffered substantial losses and wish to serve as lead plaintiff in a securities class action, or have questions about securities class action settlements, or just general questions about your rights as a shareholder, please contact attorney Timothy L. Miles of the Law Offices of Timothy L. Miles, at no cost, by calling 855/846-6529 or via e-mail at [email protected]. (24/7/365).
Timothy L. Miles, Esq.
Law Offices of Timothy L. Miles
Tapestry at Brentwood Town Center
300 Centerview Dr. #247
Mailbox #1091
Brentwood,TN 37027
Phone: (855) Tim-MLaw (855-846-6529)
Email: [email protected]
Website: www.classactionlawyertn.com
Facebook Linkedin Pinterest youtube
Visit Our Extensive Investor Hub: Learning for Informed Investors