Introduction to Asset Misappropriation Red Flags
- Asset misappropriation red flags: Represent critical warning indicators that frequently remain undetected until substantial financial damage occurs within organizations.
- Detection Timeline Matters: The ACFE’s 2024 Report to the Nations reveals that fraud cases continuing undetected beyond five years generate median losses of $875,000. Schemes discovered within six months produce median losses of merely $30,000. This stark contrast demonstrates the essential nature of early warning recognition systems.
- Asset Misappropriation Defined: Encompasses the theft or misuse of organizational physical and digital assets, creating substantial threats to business operations. Nearly 50% of internal fraud cases occur through either inadequate internal controls or deliberate circumvention of existing control systems. These control failures create environments where fraudulent activities flourish undetected.
High-Risk Department Analysis
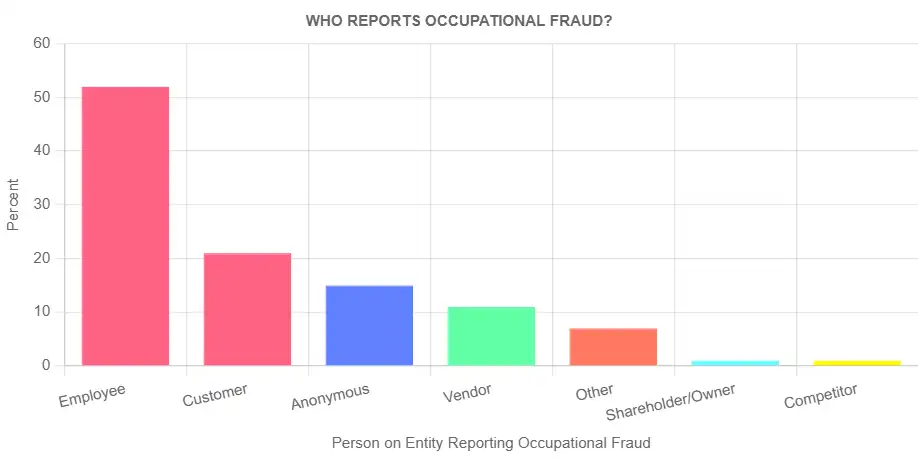
- Vulnerable Departments: Five departments account for more than half of all documented fraud cases: Operations (14%), Accounting (12%), Sales (12%), Customer Service (9%), and Executive/Upper Management (9%).
- Executive Impact Multiplier: Executives commit fraud less frequently than employees, yet the financial devastation they cause exceeds employee fraud by approximately six times. Wheeler-dealer attitudes and financial distress among personnel directly correlate with increased potential loss magnitudes.
Primary Warning Indicators
- Behavioral Red Flags: Provide the earliest detection opportunities for potential fraudulent activities. These indicators include unexplained shortages, unauthorized transactions, altered records, excessive resource utilization, and employees living beyond their documented means.
- Pattern Recognition: Identifies these warning signs before they escalate into catastrophic financial losses that can permanently damage organizational stability and market reputation.
Essential Guide Components
- Critical Coverage Areas: This guide examines the most significant red flags across behavioral, transactional, and operational domains while identifying high-risk roles and demonstrating how fraud duration directly impacts financial consequences.
- Organizational Protection: Understanding these warning signs empowers organizations to implement effective detection systems before becoming another casualty in occupational fraud statistics.
COMMON METHODS OF ASSET MISAPPROPRIATION
Behavioral Red Flags of Asset Misappropriation
- Behavioral Warning Signs: Serve as the primary defense mechanism against asset misappropriation schemes before they escalate into catastrophic financial losses.
- Early Detection Advantage: These indicators consistently appear before fraud discovery, enabling organizations to minimize financial damage through proactive identification systems.
Critical Behavioral Patterns That Signal Fraud Risk
- Employee Behavior Analysis: Provides the earliest fraud detection opportunities within organizational environments. The Association of Certified Fraud Examiners (ACFE) has documented consistent behavioral patterns across multiple research studies spanning more than a decade.
- Statistical Evidence: The 2024 Report to the Nations reveals that 85% of fraudsters displayed at least one behavioral red flag during their criminal activities.
The Six Primary Behavioral Red Flags That Persist Across All Studies:
- Living Beyond Documented Means: Represents the most prevalent indicator at 42%, maintaining its position as the top warning sign in every ACFE study since 2008. Fraudulent employees typically display affluence inconsistent with their known compensation, including expensive automobiles, luxury purchases, and extravagant vacation spending.
- Personal Financial Distress: Appears in 26% of documented cases, where financial pressures drive individuals toward fraudulent activities. These circumstances include substantial debt histories, inability to meet essential financial obligations, or repeated borrowing from workplace colleagues.
- Inappropriate Vendor or Customer Relationships: Present in 19% of cases, this warning indicator often reveals collusion schemes or conflicts of interest, particularly among male perpetrators.
- Control Issues and Duty Hoarding: Occurring in 15% of cases, employees who consistently refuse to delegate responsibilities or share critical tasks may be concealing ongoing fraudulent schemes.
- Defensive or Suspicious Behavior: Observed in 13% of cases, heightened aggression or defensiveness when questioned about work activities frequently signals underlying deceptive behavior.
- Wheeler-Dealer Mentality: Also appearing in 13% of cases, this characteristic describes individuals who consistently employ cunning or unscrupulous approaches to business transactions.
- Historical Consistency: These six behavioral indicators have remained the most frequently observed warning signs in every ACFE research study since 2008, demonstrating remarkable statistical stability.
Secondary Warning Signs in Workplace Performance
- Performance-Related Indicators: Beyond primary behavioral patterns, employees engaged in asset misappropriation frequently exhibit additional workplace behaviors requiring immediate attention. Performance-related issues appeared in 52% of documented fraud cases.
- Workplace Behavior Anomalies:
- Employees who consistently refuse vacation time or sick leave, potentially fearing scheme discovery during their absence
- Workers who establish unusual schedule patterns, arriving early, staying late, or working weekends without legitimate business justification
- Individuals demonstrating sudden excessive absenteeism (13%) or chronic tardiness (12%)
- Employees receiving poor performance evaluations (13%) or experiencing denied raises or promotions (10%)
- Team members expressing excessive fear regarding job security (12%)
- Personal Life Circumstances as Risk Factors
- Personal Life Indicators: Manifest as warning signs in 63% of fraud cases, with fraudsters exhibiting red flag behaviors connected to their personal circumstances.
- Critical Personal Risk Factors:
- Excessive family or peer pressure for financial success (19%)
- Instability in personal life circumstances (15%)
- History of legal problems (13%)
- Social isolation patterns (13%)
- Substance abuse or gambling addiction problems (8%)
- Divorce proceedings or family conflicts (6%)
- High-Impact Correlations: Specific indicators correlate with substantially elevated financial losses. The behavioral red flag associated with the highest median loss ($617,000) involves excessive organizational pressure. Past legal problems, wheeler-dealer attitudes, and bullying or intimidation behaviors also correlate with more substantial financial damages.
Strategic Detection and Prevention Implementation
- Organizational Vigilance Requirements: Identifying these warning signs demands systematic vigilance across all organizational levels and departments.
Essential Detection Strategies:
- Robust Whistleblower Program Implementation: Tips consistently represent the most effective fraud detection method, identifying 47% of fraud cases.
- Comprehensive reporting systems: Transform entire workforces into detection mechanisms when employees understand proper suspicious activity reporting procedures.
- Management and Staff Training Programs: Regular fraud awareness education that specifically addresses behavioral red flags significantly increases detection probability.
- Management personnel: Must maintain particular attention toward lifestyle changes that appear inconsistent with documented income sources.
- Employee Knowledge Systems: Understanding normal behavioral patterns enables easier identification of unusual changes.
- Multiple Red Flags: Appearing simultaneously in the same individual require immediate elevated scrutiny.
- Instinct-Based Analysis: Employees displaying obvious lifestyle inconsistencies—such as a $40,000 annual earner driving a $90,000 automobile—warrant additional investigation.
- Anonymous complaints: Or persistent tips pointing toward specific individuals should trigger systematic data collection and formal investigation procedures.
- Mandatory Vacation Policies: Many fraudulent schemes have been discovered when perpetrators finally miss work and cannot prevent incriminating evidence from surfacing.
- Organizational Climate Assessment: Beyond individual behaviors, organizational warning signs include absence of ethical leadership, missing documented policies, poor employee morale, and elevated turnover rates.
- Investigation Protocols: The presence of warning signs does not automatically confirm fraudulent activity. However, when multiple red flags appear, particularly combined with transactional or operational anomalies, organizations must conduct thorough investigations to determine whether fraud has occurred or continues.
Transactional Red Flags in Occupational Fraud
- Transaction Analysis: Financial transactions provide critical forensic evidence of potential fraud within organizations before schemes escalate into catastrophic financial losses.
- Evidence Trail: Transaction records frequently reveal asset misappropriation patterns that behavioral indicators alone cannot detect, creating essential documentation for fraud prevention and prosecution.
Unusual Payment Patterns and Skimming
Skimming Schemes: Represent among the most prevalent forms of asset misappropriation, occurring when employees steal cash before it enters accounting systems. These thefts create minimal paper trails, making detection particularly challenging for organizations without robust monitoring systems.
Critical Payment Anomalies:
- Infrequent Bank Deposits: Despite regular cash sales activity, indicating potential cash diversion before recording.
- Inventory-Sales Discrepancies: Physical inventory counts failing to match recorded sales suggest employees selling products without transaction documentation.
- Bank Balance Fluctuations: Consistent variations without clear business justification warrant immediate investigation.
- Cash Shortage Patterns: Recurring discrepancies associated with specific employees indicate targeted theft activities.
- Round Number Transactions: Unusual compared to normal business patterns, suggesting manufactured or manipulated entries.
- Industry-Specific Manifestations: Retail environments experience particular vulnerability to cash skimming schemes where employees pocket payments without recording sales. Fraud investigators employ surprise physical inventory counts to verify whether inventory levels align with recorded sales.
- Banking Detection Systems: Advanced automated monitoring identifies transaction irregularities including unexpected location changes, mismatched IP addresses, and sudden large withdrawals. Comprehensive manual investigations follow suspicious activity detection to examine collected data for potential fraud patterns.
Duplicate or Unauthorized Transactions
- Duplicate Payment Schemes: Create substantial threats to financial integrity through both unintentional errors and deliberate fraud, involving multiple payments for single invoices that generate significant financial losses.
- Unauthorized Transaction Indicators:
- Multiple Identical Payments: Same amounts, invoice numbers, or dates appearing across different payment records.
- Purchase Order Violations: Payments exceeding total purchase order amounts without proper authorization.
- Non-Original Invoice Submissions: Documents other than original invoices submitted for payment processing.
- Missing Documentation: Invoiced goods or services lacking proper purchase order documentation.
- Suspicious Round Numbers: Payments appearing unusual within normal business circumstances.
- Sophisticated Execution Methods: Fraudsters create invoices with slight variations including altered invoice numbers or dates. Compliance officers must maintain vigilance regarding these discrepancies, which frequently exploit weaknesses in invoice processing systems.
- Financial Impact Statistics: Approximately 0.05% to 0.1% of all invoices paid by organizations result in duplicate payments. Organizations utilizing accounts payable automation successfully prevent 95% of duplicate payments before processing, demonstrating automated control effectiveness in risk mitigation.
INTERNAL CONTROLS FOR START-UP COMPANIES

Red Flags in Billing and Reimbursement
- Billing Schemes: Represent the most financially damaging form of asset misappropriation. These fraudulent disbursements manipulate organizational purchasing functions to acquire nonexistent, overpriced, or unnecessary goods and services. The three primary categories encompass shell company schemes, pay-and-return schemes, and personal purchase schemes.
Billing Fraud Indicators:
- Shell Company Addresses: Post office boxes or residential addresses rather than legitimate business locations.
- Document Tampering: Invoices appearing soiled, incomplete, or altered through manipulation.
- Unfolded Invoices: Suggesting documents were never mailed through legitimate channels.
- Threshold Manipulation: Numerous invoices positioned just beneath approval thresholds.
- Vendor Information Changes: Frequent modifications in vendor names or billing addresses.
- Unknown Vendor Presence: Consistent appearance of vendors unfamiliar to organizational staff.
- Billing Pattern Alterations: Changes from bi-monthly to bi-weekly or other unusual modifications.
- Procedural Bypasses: Suppliers handled outside normal procedures without staff recognition.
- Expense Reimbursement Fraud: Creates additional organizational risk when employees submit false or modified expenses disguising personal expenditures as work-related activities. Common schemes include submitting personal expenses as business expenses, overstating actual expenses, or claiming expenses never incurred.
Prevention and Detection Strategies
Rigorous Detection Procedures: Organizations must implement cross-referencing between payment records and supporting documentation while utilizing data analytics tools for discrepancy identification. Standardized invoice processing protocols combined with clear departmental communication prove essential for preventing fraudulent billing activities.
Extended Financial Consequences: These schemes create cash flow issues when unnecessary payments deplete organizational resources. Repeated duplicate payments damage supplier relationships while potentially harming market reputation over extended periods. Organizations incur additional costs through investigations, productivity losses, and potential legal compliance expenses.
Comprehensive Defense Framework: Effective prevention requires strategic approaches including strong security measures such as encryption and regular account monitoring. Regular fraud awareness training sessions equip staff with skills necessary for red flag identification. Detection systems employing both automated tools and human oversight provide the most effective defense against transactional fraud schemes.
Operational Red Flags in Asset Misuse
- Operational warning signs: Manifest throughout daily organizational activities, frequently signaling ongoing fraud schemes before financial losses reach catastrophic levels.
- Early Detection Opportunity: These operational indicators provide tangible evidence that enables organizations to identify asset misappropriation before schemes mature into devastating financial disasters.
 Excessive Use of Company Resources: Direct Asset Theft
Excessive Use of Company Resources: Direct Asset Theft
- Resource Misappropriation: Occurs when employees utilize company property beyond legitimate professional requirements, constituting serious occupational fraud that directly depletes organizational assets.
Common Manifestations of Resource Abuse:
- Unauthorized use of company vehicles or equipment for personal activities
- Excessive or suspicious company expenses lacking proper business justification
- Employees making unusually large purchases inconsistent with documented salary levels
- Diversion of company resources toward non-business activities
- Detection Requirements: Organizations must establish proper tracking systems for physical assets and resources to identify this fraudulent behavior. Evidence demonstrates that lack of centralized operational data significantly increases vulnerability to asset misappropriation. Poor oversight of expense records creates opportunities for employees to falsify expenditures, potentially adding fictitious business lunches or other personal expenses.
- Prevention Through Controls: Organizations implementing automated workflows reduce these risks by enforcing segregation of duties through system-based role assignments. This systematic approach prevents single individuals from controlling entire resource allocation processes.
Inventory Shrinkage: Measuring the Cost of Internal Theft
- Inventory Shrinkage Defined: Represents the discrepancy between recorded inventory and actual physical counts, serving as a critical operational red flag that directly impacts organizational profitability.
- Escalating Financial Impact: Retail shrinkage rates climbed from 1.4% to 1.6% in 2022, reflecting broader security challenges facing organizations. Retail shrink projections reach USD 132.00 billion in global losses for 2024, compared to USD 112.00 billion in 2022.
Key Indicators of Inventory-Related Fraud:
- Discrepancies between physical counts and recorded inventory levels
- Unexplained increases in particular purchases or unusual ordering patterns
- Consistent shortages in specific inventory categories
- Abnormal inventory usage rates without corresponding production increases
- Unexpected fluctuations during specific employee shifts
- Theft Dominates Shrinkage Causes: Retail theft, encompassing both internal (29%) and external (37%) theft, continues dominating shrinkage statistics. When inventory disappears through shrinkage, companies lose both inventory costs and potential sales revenue.
- Operational Efficiency Impact: Organizations often raise product prices to offset inventory losses, effectively transferring theft costs to consumers. Businesses typically invest in additional security measures, including surveillance systems and personnel, further reducing profitability.
Altered Records and Missing Documentation: The Paper Trail of Fraud
- Document manipulation: Represents one of the most revealing operational indicators of asset misappropriation. Fraudsters frequently create, alter, or destroy documentation to conceal their criminal activities.
- Control Failures Enable Fraud: Nearly half of all occupational fraud cases occur through either lacking internal controls (29%) or circumvention of existing controls (20%). These control weaknesses create environments where document manipulation flourishes undetected.
Critical Document-Related Red Flags:
- Missing or altered receipts, particularly those supporting reimbursement requests
- Photocopied documents submitted instead of originals
- Inconsistencies between purchase records and actual inventory
- Excessive voided transactions or customer returns without proper documentation
- Records showing unauthorized account adjustments or write-offs
- Missing canceled checks or vendor invoices
- Fraud Scheme Variations: Document manipulation takes various forms depending on specific fraud schemes. Employees might fabricate receipts to support fraudulent reimbursement requests or destroy sales records to conceal cash skimming. This tampering creates apparent gaps between operational activities and documented records.
- Legal Significance: Federal law specifically prohibits the concealment, destruction, or falsification of recorded information relating to financial affairs. Organizations must recognize that individuals with abilities to create and edit financial records possess greater opportunities to commit fraud.
- Review Procedure Failures: Inadequate review procedures often facilitate document manipulation. When expense reimbursement requests receive approval from individuals unfamiliar with policy requirements, fraudsters can submit duplicate receipts for identical transactions, resulting in multiple payments.
- Comprehensive Protection Strategy: Operational red flags provide tangible evidence of potential asset misappropriation. Robust inventory management systems, clear documentation requirements, and proper oversight of company resources enable organizations to identify these warning signs before they escalate into major financial losses.
High-Risk Roles and Departments
Organizational Vulnerability Assessment
- Certain positions and departments create substantially higher fraud risks than others within modern organizations. Identifying these vulnerable areas enables targeted monitoring and control implementation designed to protect valuable assets from misappropriation schemes.
The Five-Department Risk Concentration
- Fraud Distribution Patterns: The 2024 ACFE report demonstrates that more than half of all fraud cases originate from merely five organizational areas:
- Operations (14%)
- Accounting (12%)
- Sales (12%)
- Customer Service (9%)
- Executive/Upper Management (9%)
- Accounting Department Vulnerabilities: Personnel working within accounting functions require particular scrutiny due to their direct access to financial data and company funds. These employees possess intimate understanding of financial systems, creating unique opportunities to manipulate records without detection.
- Industry-Specific Risk Patterns: Banking and financial services experienced the highest number of fraud cases (305), followed by manufacturing (175), government and public administration (171), and healthcare (117). Asset misappropriation characteristics vary significantly across organizational levels—lower-level employees and managers most commonly target corporate assets, while higher-level trusted positions including lawyers and financial advisors represent greater risk for client asset theft.
The Tenure-Trust Paradox
- Long-Term Employee Threat: Most occupational fraud schemes are executed by individuals who have worked within organizations for more than ten years. This counterintuitive reality highlights critical vulnerabilities in many fraud prevention systems that rely heavily on tenure-based trust.
- Financial Impact Correlation: Employees with ten or more years of experience generate median losses of $250,000, while perpetrators with one year or less experience cause median losses of only $50,000. Experience within an organization directly magnifies potential financial damage through three primary factors:
- Greater access to sensitive information and resources
- Enhanced understanding of control weaknesses and exploitation methods
- Increased opportunities to manipulate systems without detection
- Behavioral Pattern Distinctions: Long-tenured fraudsters demonstrate higher likelihood of collusion and exhibit six specific red flags with greater frequency: living beyond their means, unusually close association with vendors/customers, control issues and unwillingness to share duties, plus irritability, suspiciousness, or defensiveness. The direct correlation between employee tenure and financial loss magnitude relates to both increased trust levels and expanded opportunity access.
Authority-Access Risk Multiplication
- Executive Impact Disparity: Position and authority dramatically amplify fraud potential within organizations. Owners and executives generate median losses approximately seven times greater than employees ($459,000 versus approximately $60,000). Executive fraud produces median losses of $500,000 compared to manager fraud ($184,000) and employee fraud ($60,000).
- Collaboration Risk Amplification: Multiple perpetrators working together create substantially larger losses. Fraud schemes executed by three or more individuals generate median losses more than four times greater than single-person schemes. This collaboration frequently crosses departmental boundaries, significantly complicating detection efforts.
Control Weakness Indicators: Several organizational deficiencies markedly increase fraud vulnerability:
- Lack of segregation of duties
- Inadequate physical safeguarding of assets
- Missing asset reconciliation processes
- Insufficient management review
- Poor personnel competency
- Education-Sophistication Correlation: Higher education levels among perpetrators typically correlate with larger fraud losses. This pattern aligns with the broader principle that increased capability and knowledge enhance fraud scheme sophistication.
- Trust Without Controls: Excessive trust combined with inadequate internal controls creates dangerous fraud opportunities. Organizations must establish robust systems where financial information access remains limited to essential personnel only.
Duration and Cost Implications of Asset Misappropriation Fraud

- Time Becomes the Enemy: Asset misappropriation schemes demonstrate a direct relationship between detection timeline and financial devastation. The longer fraudulent activities continue undetected, the more catastrophic their impact becomes on organizational stability and market confidence.
Fraud Scheme Duration: The Critical Vulnerability Window
- Average Detection Timeline: Occupational fraud schemes persist for an average of 12 months before discovery. This duration has remained remarkably consistent across recent studies, demonstrating no improvement despite technological advances in detection capabilities.
- Active Concealment Strategies: Fraudsters employ sophisticated methods to extend their schemes undetected. Perpetrators typically create or alter physical and electronic documents to hide evidence while exploiting weak or nonexistent internal controls. Organizational overconfidence in long-tenured employees reduces scrutiny, creating extended vulnerability periods.
- Control Implementation Impact: Organizations implementing robust anti-fraud controls experience 14% to 50% reduction in scheme duration. This shortened detection timeline directly correlates with reduced financial damage and organizational preservation.
The Devastating Cost Escalation Pattern
- Duration-Loss Correlation: The relationship between fraud duration and financial impact reveals staggering patterns. Frauds lasting six months or less result in median losses of approximately $30,000, while schemes continuing beyond five years cause median losses of $875,000. This represents a devastating 29-fold increase in financial damage based solely on detection timeline.
- Escalating Monthly Damage: The average loss per month increased from $8,300 in 2022 to $9,900 in 2024, reflecting both inflation and increasingly sophisticated schemes. Organizations typically lose 5% of annual revenue to fraud, creating cumulative damage that compounds over extended periods.
Scheme Evolution Factors:
- Increasing Sophistication: Perpetrators gain confidence and expand their methods as initial attempts succeed undetected.
- Method Multiplication: Successful fraudsters often expand to multiple fraud techniques once they establish operational patterns.
- Collaborative Expansion: Additional collaborators become involved, expanding the scheme’s scope and financial impact.
- Growing Financial Demands: Perpetrators require larger thefts to maintain their deceptive lifestyles or address escalating personal financial pressures.
- Early Detection Value: Fraud schemes discovered through active surveillance methods lasted merely six months with median losses of $65,000, versus substantially larger losses for passively detected schemes.
Real-World Consequences: Case Studies in Prolonged Asset Misappropriation
- Financial Trust Bank Case: A senior manager misappropriated over $2 million during a three-year period. The perpetrator exploited weak internal controls, transferring small amounts regularly to personal accounts—a technique specifically designed to avoid detection thresholds. This case demonstrates how sophisticated perpetrators manipulate control weaknesses to extend their schemes.
- COVID-19 Relief Fund Fraud: A Louisiana woman misappropriated more than $780,000 by submitting false attestations. These funds supported personal purchases including real estate, luxury vehicles, and recreational boats. Authorities eventually seized over $500,000 from her accounts, highlighting both the scheme’s scale and the challenge of complete recovery.
- Category-Specific Duration Patterns:
- Billing Schemes: Typically continue for 18 months with median losses of $100,000.
- Corruption Schemes: Persist approximately 13 months with median losses reaching $200,000.
- Noncash Misappropriation: Show shorter durations (12 months) with correspondingly lower median losses ($66,000).
- Detection Method Impact: Organizations employing active detection strategies identify fraud schemes significantly earlier, substantially reducing financial damage. This emphasizes the critical importance of implementing proactive monitoring systems rather than relying on passive discovery methods that allow schemes to compound into catastrophic losses.
- Prevention Through Vigilance: The evidence demonstrates that fraud duration directly determines organizational survival. Companies that recognize asset misappropriation red flags early protect themselves from the escalating financial devastation that destroys market confidence and threatens operational viability.
Asset Misappropriation Red Flags: Comparative Analysis Framework
Risk Category Assessment: Organizations must understand the distinct characteristics, financial implications, and detection methodologies across different types of asset misappropriation red flags. This comparative analysis reveals critical patterns that enable targeted prevention strategies.
Behavioral Warning Indicators
Statistical Foundation: Research demonstrates that 85% of fraudsters display at least one behavioral red flag during their criminal activities .
Primary Characteristics:
- Living beyond means: Present in 42% of cases, representing the most prevalent indicator
- Financial difficulties: Observed in 26% of documented fraud schemes
- Close vendor associations: Appearing in 19% of cases, particularly among male perpetrators
- Control issues: Manifesting in 15% of cases through unwillingness to share duties
- Defensiveness: Exhibited by 13% of fraudsters when questioned about work activities
Financial Consequences: Excessive organizational pressure correlates with the highest median loss of $617,000, demonstrating how workplace stress amplifies fraudulent behavior .
Detection Strategies: Whistleblower programs, regular fraud awareness training, and mandatory vacation policies provide the most effective behavioral detection mechanisms.
Transaction-Based Warning Signs
Statistical Prevalence: Approximately 0.05% to 0.1% of organizational invoices result in duplicate payments, creating substantial financial exposure .
Critical Indicators:
- Unusual payment patterns: Including infrequent bank deposits despite regular cash sales
- Duplicate transactions: Featuring identical amounts, invoice numbers, or processing dates
- Suspicious billing patterns: Involving shell companies or altered documentation
- Irregular reimbursements: Submitted without proper supporting documentation
Financial Impact: Automated controls prevent 95% of duplicate payments before processing, demonstrating the effectiveness of technological solutions in reducing transactional fraud .
Prevention Methods: Cross-referencing payment records, data analytics tools, and standardized invoice processing protocols create multiple layers of transactional protection.
Operational Risk Patterns
Industry Data: Retail shrinkage increased from 1.4% to 1.6% in 2022, reflecting escalating operational vulnerabilities across industries .
Key Characteristics:
- Excessive resource use: Involving unauthorized utilization of company vehicles or equipment
- Inventory discrepancies: Between physical counts and recorded inventory levels
- Altered documentation: Including missing receipts or photocopied documents
- Unusual ordering patterns: Inconsistent with normal business requirements
Global Impact: Retail shrink projects to reach $132 billion in losses during 2024, compared to $112 billion in 2022 .
Control Mechanisms: Automated workflows, surprise physical inventory counts, and strict documentation requirements provide operational fraud detection capabilities.
Departmental Risk Assessment
Concentration Analysis: Five departments account for 56% of all documented fraud cases across organizational structures .
High-Risk Areas:
- Operations: Responsible for 14% of fraud cases
- Accounting: Contributing 12% of documented schemes
- Sales: Generating 12% of organizational fraud
- Customer Service: Accounting for 9% of cases
- Executive Management: Representing 9% of fraud occurrences
Executive Multiplier Effect: Executive-level fraud produces median losses of $459,000 compared to $60,000 for employee-level schemes, representing a seven-fold increase in financial damage .
Risk Mitigation: Segregation of duties, limited access controls, and enhanced management review procedures address departmental vulnerabilities.
Duration and Financial Correlation
Scheme Timeline: Average fraud schemes persist for 12 months before detection, demonstrating the extended vulnerability periods organizations face .
Critical Characteristics:
- Active concealment: Through document manipulation and evidence destruction
- Document manipulation: Creating false records to obscure fraudulent activities
- Control exploitation: Taking advantage of weak or nonexistent oversight systems
Financial Progression: Schemes detected within six months result in $30,000 median losses, while those continuing beyond five years cause $875,000 median losses—a 29-fold increase based solely on detection timing .
Strategic Prevention: Active surveillance methods and proactive controls reduce scheme duration by 14% to 50%, directly limiting financial exposure and organizational damage .
Essential Organizational Protection Against Asset Misappropriation
- Asset misappropriation schemes: Create devastating threats to organizational stability across all industries, yet early recognition of warning indicators dramatically reduces potential financial damage.
- Detection System Effectiveness: Organizations implementing robust detection frameworks identify fraudulent schemes months or years before those relying on passive discovery methods, preventing the escalation of minor incidents into catastrophic financial losses.
Critical Warning Categories
- Behavioral Indicators: Fraudsters consistently exhibit recognizable patterns before schemes cause significant damage. Living beyond documented means, experiencing financial difficulties, and maintaining unusually close vendor relationships represent primary misconduct indicators that demand immediate attention.
- Transactional Evidence: Unusual payment records, duplicate transactions, and suspicious billing activities provide concrete evidence of ongoing fraudulent activities. Data analytics tools combined with standardized invoice processing protocols create essential barriers against unauthorized financial manipulation.
- Operational Manifestations: Excessive resource utilization, inventory shrinkage, and altered documentation represent tangible proof of asset misappropriation occurring within organizational operations.
Risk Assessment Priorities
Departmental Vulnerability: Operations, accounting, sales, customer service, and executive management account for the majority of documented fraud cases. Executive-level schemes, though less frequent, generate approximately six times greater financial damage than employee-level fraudulent activities.
Duration Impact Analysis: Schemes continuing six months or less result in median losses of approximately $30,000, while those persisting beyond five years cause median losses of $875,000. Active surveillance methods substantially reduce both scheme duration and financial consequences.
Organizational Protection Framework
Essential Prevention Components:
- Monitoring Systems: Establish surveillance across all organizational levels to identify suspicious activities before they escalate
- Training Programs: Implement regular fraud awareness education enabling employees to recognize and report warning indicators
- Control Structures: Maintain strong internal controls with proper segregation of duties preventing single-person manipulation
- Reporting Mechanisms: Create whistleblower programs encouraging disclosure of suspicious activities without fear of retaliation
- Analytical Tools: Deploy data analytics systems identifying unusual transactional patterns indicating potential fraud
Organizational Transformation: Understanding these warning indicators transforms entire organizations into effective fraud detection systems, significantly reducing vulnerability to asset misappropriationwhile protecting financial resources from individuals who might exploit their positions of trust.
Prevention Investment: The cost of implementing these protective measures proves substantially less than the financial devastation caused by undetected fraudulent schemes that continue unabated for extended periods.
Key Takeaways
Understanding asset misappropriation red flags can save organizations from devastating financial losses, with early detection reducing median losses from $875,000 to just $30,000.
• Behavioral warning signs appear first: 85% of fraudsters display red flags like living beyond means (42%) or financial difficulties (26%) before schemes are discovered.
• High-risk departments need extra scrutiny: Operations, accounting, sales, customer service, and executive management account for 56% of all fraud cases.
• Long-tenured employees pose the greatest threat: Employees with 10+ years cause median losses of $250,000 versus $50,000 for those with under one year.
• Time is critical for damage control: Fraud schemes lasting over 5 years cause 29 times more financial damage than those caught within 6 months.
• Executive fraud is most costly: While less frequent, executive-level fraud causes approximately 6 times more financial damage ($459,000 vs $60,000) than employee fraud.
The most effective protection combines whistleblower programs, mandatory vacation policies, data analytics tools, and comprehensive fraud awareness training. Organizations implementing active surveillance methods reduce scheme duration by 14-50%, directly translating to substantial cost savings and asset protection.
FAQs
Q1. What are the most common red flags of asset misappropriation? Common red flags include employees living beyond their means, unexplained cash shortages, altered financial records, excessive use of company resources, and unusual transactions or payment patterns.
Q2. How does employee behavior indicate potential asset misappropriation? Behavioral indicators may include reluctance to take vacations, working unusual hours, being overly protective of records, displaying a “wheeler-dealer” attitude, or showing signs of financial stress or addiction issues.
Q3. Which departments are most vulnerable to asset misappropriation? The departments at highest risk typically include Operations, Accounting, Sales, Customer Service, and Executive/Upper Management. These areas often have greater access to assets and financial systems.
Q4. Why are long-tenured employees considered high-risk for fraud? Long-tenured employees often have in-depth knowledge of company systems, greater access to resources, and may be subject to less scrutiny due to established trust, potentially increasing their ability to commit and conceal fraud.
Q5. How does the duration of a fraud scheme impact financial losses? The longer a fraud scheme continues undetected, the greater the financial damage. Schemes lasting over five years can result in median losses of $875,000, compared to just $30,000 for those detected within six months.
Contact Timothy L. Miles Today for a Free Case Evaluation
If you suffered substantial losses and wish to serve as lead plaintiff in a securities class action, or have questions about securities class action settlements, or just general questions about your rights as a shareholder, please contact attorney Timothy L. Miles of the Law Offices of Timothy L. Miles, at no cost, by calling 855/846-6529 or via e-mail at tmiles@timmileslaw.com. (24/7/365).
Timothy L. Miles, Esq.
Law Offices of Timothy L. Miles
Tapestry at Brentwood Town Center
300 Centerview Dr. #247
Mailbox #1091
Brentwood,TN 37027
Phone: (855) Tim-MLaw (855-846-6529)
Email: tmiles@timmileslaw.com
Website: www.classactionlawyertn.com
Facebook Linkedin Pinterest youtube
Visit Our Extensive Investor Hub: Learning for Informed Investors