Introduction to the Red Flags of Asset Misappropriation
Red Flags of Asset Misappropriation: According to an extensive research report issued by the Association of Certified Fraud Examiners (ACFE), fraud causes over $3.1 billion annually, $1,662,000 per incident with 22% consisting of losses exceeding one million.
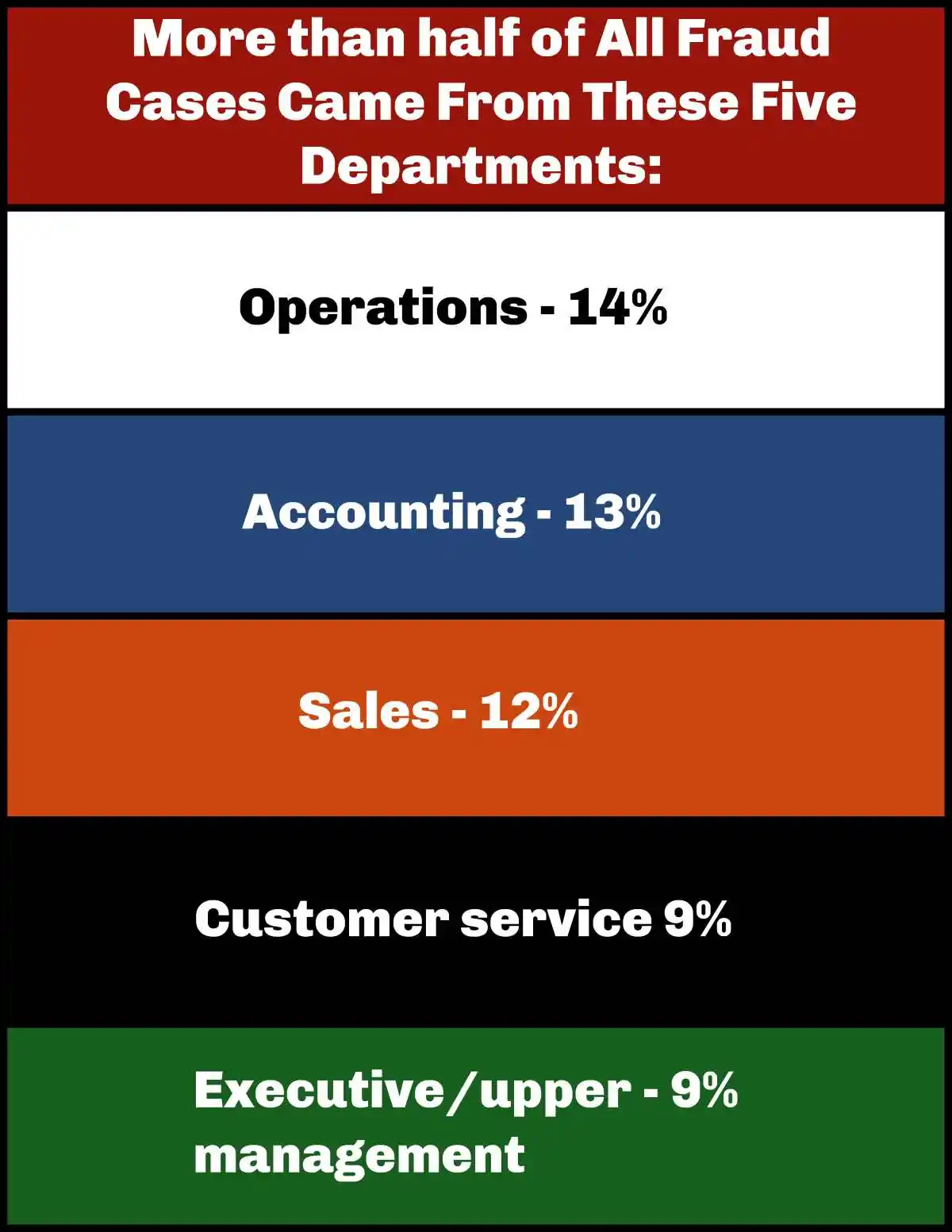
Three Main Categories of Occupational Fraud: The three main categories of occupational fraud, as defined by the ACFE, are asset misappropriation, fraudulent financial statement fraud, and corruption.
Asset Misappropriation: This comprehensive guide discusses asset misappropriation which accounts for 89% of the financial crimes, although it has the lost medial average of $120,000, as compared to financial statement fraud with a staggering $766,000 median. Corruption amounted to a median of $120,000 per year.
Three Main Categories of Occupational Fraud
1. Asset misappropriation
Asset Misappropriation: Refers to the unauthorized taking or misuse of an organization’s resources by employees or individuals who have access to them. This type of fraud can include stealing cash, inventory, or other tangible and intangible assets, and it often occurs without the knowledge or consent of the organization.
Most Common: This is the most common type of occupational fraud and involves an employee stealing or misusing an organization’s resources for personal use. While it is the most frequent type of fraud, it typically results in the lowest median losses.
Examples include:
- Theft of cash or inventory: Taking physical goods or money from the company.
- Fraudulent billing: Creating fake invoices to generate payments to a phantom vendor or a personal account.
- Fictitious expense reimbursements: Submitting false claims for business expenses.
- Data Theft: Data theft is the practice of employees utilizing sensitive company information for their own personal gain
- Check Tampering: Involves an employee altering a check given to the company so that they funds can be deposited into one of their accounts.
2. Financial statement fraud
Examples include:
- Overstating revenues: Recording fictitious sales or recognizing revenue prematurely to inflate profits.
- Understating expenses or liabilities: Concealing costs or obligations to make the company’s financial performance look better.
- Improper asset valuation: Artificially inflating the value of a company’s assets on the balance sheet.
3. Corruption
Examples include:
- Bribery: Offering, giving, receiving, or soliciting something of value to influence a business decision.
- Conflicts of interest: An employee having an undisclosed financial or other interest in a transaction that could compromise their judgment.
- Kickbacks: A vendor paying an employee a percentage of the money they received from the employer.
Red Flags of Assett Misappropriation
Behavioral red flags
- Living beyond one’s means: The employee has a suddenly improved or lavish lifestyle that does not match their known income.
- Financial difficulties: An employee may be driven t commit fraud due to personal financial pressure, such as from heavy debt, legal issues, or addiction.
- Controlling or secretive behavior: The employee is unwilling to share duties, take vacation, or allow others to review their work. This is often done to prevent their fraud scheme from being discovered.
- Unusual close association with a vendor or customer, which could suggest a conflict of interest or collusion
- Irritability or defensiveness when questioned about their work or transactions.
- Working excessive or unusual hours when no one else is around, to carry out or conceal a fraudulent scheme.
Organizational and control-related red flags
- Inadequate segregation of duties: A single person has control over all parts of a financial transaction, such as authorizing, processing, and reconciling it.
- Poor physical safeguards: Cash, inventory, or equipment are not properly secured.
- Lack of management oversight, particularly for remote locations or unsupervised staff.
- Missing or altered documents, such as invoices, receipts, or shipping records.
- No mandatory vacation policy: Schemes are often uncovered when the fraudster is away from the office and someone else takes over their duties.
- High employee turnover and low morale.
Financial and accounting red flags
- Unexplained shortages or discrepancies in cash, inventory, or other assets.
- Untimely or inaccurate bank reconciliations and financial reports.
- Large number of write-offs, such as customer accounts being written off as uncollectible.
- High volume of purchases from a new vendor or payments to a vendor with an address matching an employee’s.Numerous journal entries or other adjustments in a purchase ledger or suspense account.
- Significant increases in expenses without a corresponding increase in sales or business activity.
Expense report red flags
- Duplicate claims or expenses that are submitted multiple times, sometimes with minor alterations.
- Missing or vague documentation for expenses, such as incomplete receipts or receipts that are photocopied.
- Amounts just below approval thresholds, which suggests an attempt to avoid scrutiny.
- Claims for personal expenses that are mischaracterized as business-related.
- Inflated mileage or meal costs, with receipts that don’t match the claimed amount
- Submissions at unusual times, such as late at night or on weekends.
The Use of Data Analytics to Detect Red Flags for Asset Misappropriation
Schemes involving cash
- Skimming: Data analytics can identify unusual trends in sales or accounts receivable data.
- Decreased cash as a percentage of assets: A downward trend can signal that cash is being diverted before being recorded.
- Higher-than-average accounts receivable write-offs: A disproportionate number of uncollectible accounts can indicate that payments have been intercepted.
- Out-of-sequence cash receipts: Analytics can search the cash receipts journal for gaps in pre-numbered receipts, suggesting that some payments were not recorded.
- Larceny: Data analytics can compare different records to pinpoint discrepancies in cash handling.
- Mismatch of cash receipts and deposits: Comparing the cash receipts journal to bank deposit slips can reveal if cash was stolen before being deposited.
Excessive voids or refunds: Analytics can summarize voids and refunds by sales clerk and flag employees with a high number of such transactions.
- Check tampering: Analytics can scrutinize the check register for irregularities.
- Duplicate or missing check numbers: Missing numbers can indicate that physical checks have been stolen, while duplicate numbers can signal altered records
- Duplicate payments: Searching for checks with identical amounts and dates but paid to different payees can reveal tampered check
- Unusual payee names: Checks made out to employees for reasons other than payroll, or to “cash,” can indicate check tampering
Schemes involving fraudulent billing and payroll
- Fictitious vendor schemes: Analytics can cross-reference different databases to uncover fake vendors.
- Matching employee and vendor information: Comparing vendor data (address, bank account, tax ID) with employee information can uncover a fraudulent vendor created by an employee.
- Vendors with incomplete profiles: Analytics can flag vendors with missing information, such as tax IDs or telephone numbers.
- Unusual spending with a new vendor: A sudden high volume of purchases from a new vendor should be automatically flagged for review.
- “Ghost employee” schemes: Data analytics tests can detect payroll fraud by cross-referencing employee records.
- Duplicate bank account or address: Multiple employees receiving deposits to the same bank account or sharing an address is a red flag.
- Terminated employees on the payroll: Comparing payroll records with an up-to-date list of active employees can reveal “ghosts” who are still receiving payments.
- Employees with no vacation time: Fraudsters who need constant access to systems may avoid taking time off. This can be flagged by cross-referencing payroll and time-off records.
- Expense reimbursement schemes: Analytics can test expense reports against company policy and employee data.
- Round-sum reimbursements: Expense reports with frequent or large round-sum amounts can signal fictitious or inflated expenses.
- Missing or duplicate expenses: Analytics can identify missing receipts or detect duplicate claims for the same expense.
- Expenses just below approval threshold: Scrutinizing expenses that consistently fall just under the limit requiring higher approval can reveal an attempt to bypass controls.
- Inventory theft (larceny): Data analytics helps reconcile inventory counts and identify unusual transactions.
- Discrepancies in inventory counts: Comparing physical inventory counts to records can reveal inventory shortages.
- High scrap or write-off rates: An unusually high volume of inventory being sent to scrap could be a cover for theft.
- Adjustments to inventory by a single clerk: Analytics can stratify inventory adjustments by employee and flag those with an unusually high number of adjustments.
- Fixed asset fraud: Analytics can monitor the sale and disposal of fixed assets.
- Sales at below depreciated value: Selling fixed assets for significantly less than their recorded value can indicate improper disposal or kickbacks.
- Sales before end of depreciation cycle: Assets sold long before the end of their useful life should be investigated.
Advanced analytical techniques
- Anomaly detection: Machine learning algorithms can automatically identify transactions that deviate significantly from a baseline of normal behavior.
- Benford’s Law analysis: This statistical test flags unnatural patterns in the first digits of numerical data, such as invoices, which is often a sign of manufactured or falsified numbers.
- Link analysis: Using graph technology, analysts can visualize relationships between different entities (employees, vendors, transactions) to uncover hidden fraud rings or connections.
- Predictive modeling: By analyzing historical fraud cases, machine learning models can be trained to predict the likelihood of a transaction being fraudulent in real time, preventing loss before it happens
Behavioral red flags
- Living beyond one’s means: An employee’s lifestyle suddenly becomes lavish or improves beyond what their known income can support, such as purchasing expensive cars or taking luxury trips.
- Personal financial pressure: An employee may be driven to commit fraud by personal debt, medical emergencies, divorce, or gambling problems.
- Resistance to sharing duties: An employee may refuse to take vacations or share responsibilities, fearing that someone else will discover their fraudulent activity while they are away.
- Unusual work habits: This can include working excessive, unexplained overtime, often during off-hours, to carry out or conceal a fraudulent scheme.
- Defensiveness or irritability: An employee may become noticeably defensive, secretive, or irritable when questioned about their work, specific transactions, or company procedures.
- Close vendor relationships: An employee may have an unusually close association with a vendor or customer, which could indicate collusion for kickbacks or billing schemes.
- Bullying or intimidation: Employees may use these tactics to deter colleagues from scrutinizing their work or reporting irregularities.

Organizational and control-related red flags
- Lack of segregation of duties: One person having control over multiple steps in a financial process—such as authorizing payments, recording them, and reconciling bank statements—is a major vulnerability.
- Management override of controls: Management may circumvent or ignore established internal controls for a variety of reasons, creating an environment where a control system is only as strong as its enforcement.
- High employee turnover: A high rate of staff turnover, especially in areas like finance or inventory, can signal underlying issues or allow for poor controls to persist.
- Absence of oversight: Insufficient supervision, particularly in remote locations, allows fraudulent activity to go unnoticed.
- Poor physical safeguards: Inadequate security over assets like cash, inventory, or equipment creates a direct opportunity for theft.
- Inadequate training: A lack of proper training for staff on controls and ethical conduct can increase the risk of both intentional and unintentional fraud.
Physical and documentation red flags
- Missing or altered documents: This can include missing invoices, altered receipts, forged signatures, or the use of photocopies instead of original documents.
- Excessive inventory shrinkage: A significantly high amount of unaccounted-for inventory, beyond normal loss, can point to theft.
- Customer complaints: Frequent complaints from customers about non-payment notices, even though they have paid, can indicate that funds have been intercepted.
- Excessive voids or refunds: A higher-than-average number of voids or customer refunds handled by a specific employee could be a red flag for skimming schemes.
- Vendors with suspicious addresses: A vendor’s address matching an employee’s home address or a Post Office box can be a sign of a fictitious vendor scheme.
Key weaknesses in a company’s internal controls can create the opportunity for asset misappropriation to occur
A strong internal control environment i the first line of defense against fraud, so vulnerabilities in these systems are often exploited by employees seeking to commit theft or misuse company assets.
Segregation of duties
- Incompatible duties involve having responsibility for two or more of the following key functions:
- Authorization: Approving a transaction
- Custody: Handling the physical asset (cash, inventory)
- Record-keeping: Entering the transaction into the accounting system
- Reconciliation: Comparing records to physical assets or bank statements
- Example: If one employee is responsible for receiving cash payments, recording the payment in the accounting system, and reconciling the bank statement, they could easily take cash and cover it up by altering the records.
Management and oversight
- Inadequate supervision: Weak monitoring of employees and business processes, especially in remote locations, allows fraudulent activity to go unnoticed.
- Ineffective management review: If managers do not regularly review and approve transactions, it creates an opportunity for employees to hide fraudulent activity.
- Management override of controls: Senior leaders can bypass established internal control policies to achieve business goals or for personal gain, sending a message that controls can be ignored.
- Poor hiring practices: Inadequate background checks or screening for employees with access to assets can allow individuals with financial or behavioral red flags to be hired.
Physical and information safeguards
- Inadequate physical controls: Not locking up cash or valuable assets, using poorly guarded storage areas, or failing to restrict access to secure areas allows employees to easily steal inventory, equipment, or cash.
- Weak access controls: Insufficient or poorly monitored access to sensitive computer systems, data, and electronic records can lead to information theft or the creation of fraudulent transactions.
Recording and documentation
- Poor recordkeeping: Missing or inaccurate documentation, such as invoices, receipts, or shipping records, makes it difficult to trace transactions and compromises the audit trail.
- Lack of independent checks: Not performing regular, independent reconciliations of assets and accounts, such as bank statements, can allow discrepancies to go undetected.
- Failure to enforce mandatory vacations: Fraudulent schemes are often discovered when the perpetrator is on vacation and another employee takes over their duties. Without mandatory time off, fraudsters can maintain their schemes for longer periods.
Technology and automation
- Insufficient use of automation: Relying heavily on manual processes creates more opportunities for human error and intentional fraud.
- Failure to update technology: Outdated systems can lack the security features and automated controls needed to protect against modern threats.
- Poorly integrated systems: Disjointed or non-integrated software systems can create gaps that allow fraudulent transactions to slip through undetected
A poor “tone at the top” is a key driver of asset misappropriation because it erodes the ethical foundation of an organization and undermines the control environment. The attitude and actions of senior management and the board of directors set the standard for employee behavior. When that tone is weak, it creates opportunities for fraud through several mechanisms.
Management override of controls
- Rationalizing shortcuts: Managers who feel pressure to meet unrealistic financial targets may override controls under the guise of efficiency or speed. Employees observe this behavior and may interpret it as permission to do the same.
- Influencing accounting staff: High-level managers can coerce accounting staff into making questionable journal entries or transactions to hide theft. Staff may comply out of loyalty, fear of losing their job, or the belief that the manager is more trustworthy than the official policy.
- Hiding theft through authority: Management can use its authority to write off receivables or inflate revenue, which can be a way of concealing asset misappropriation. These overrides are hard to detect because they are performed by individuals with high levels of system access and authority.
Normalization of unethical behavior
- “They’re doing it too”: Employees often take behavioral cues from their superiors. If employees see managers exaggerating expenses, taking company property for personal use, or tolerating minor infractions, they are more likely to justify their own dishonest actions with the rationalization, “upper management is doing it as well”.
- Rewarding results over ethics: If the company culture focuses exclusively on meeting aggressive targets, employees may feel intense pressure to cut corners. A manager’s focus on profits at all costs, with no regard for the process, can motivate employees to manipulate data or engage in fraud to avoid negative consequences.
Erosion of trust and control
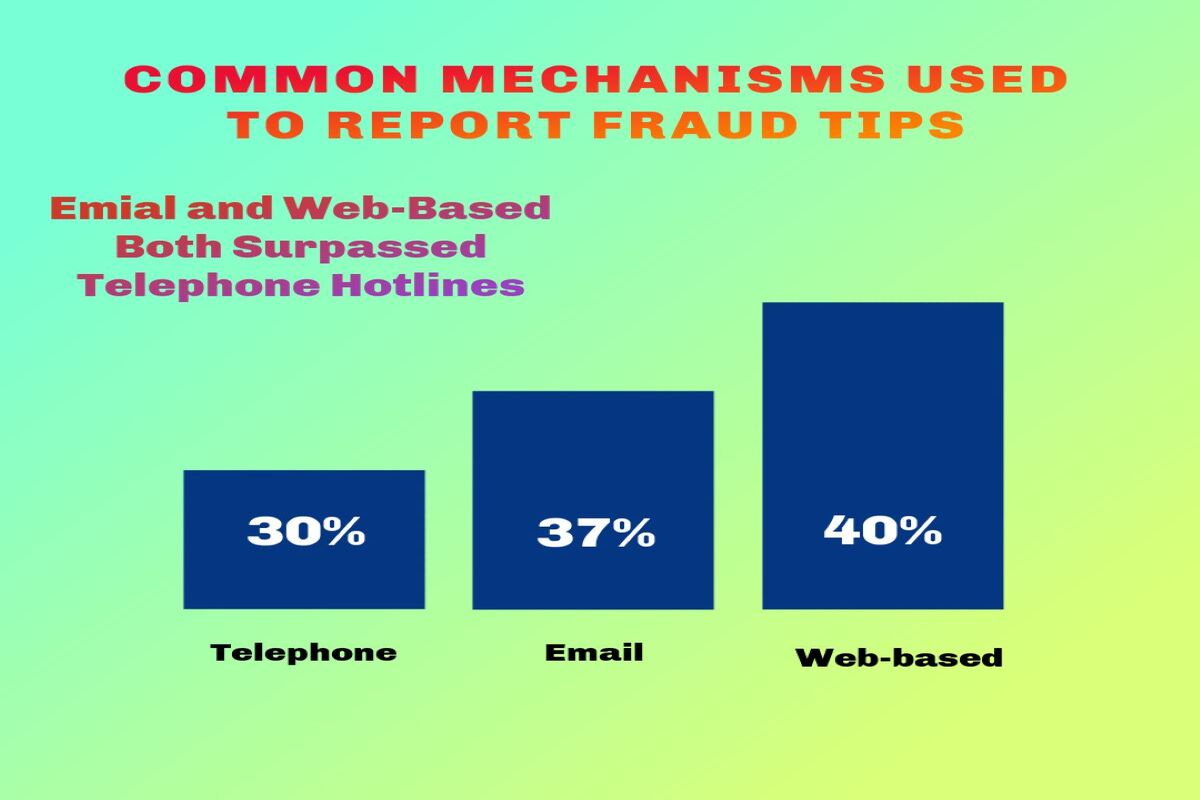
- Weakened whistleblower protections: A management team that ignores or retaliates against employees who report misconduct will destroy a company’s ethics hotline and encourage employees to remain silent. Since tips are the most common way fraud is detected, a poor tone effectively disables a key defense.
- Reduced morale and loyalty: Employees in an environment with low morale and a toxic culture feel less loyalty to the company and its goals. This reduces the rationalization barrier to committing fraud, as employees feel less guilt about hurting an organization that they feel has wronged them.
- Disregard for monitoring: When management does not take internal controls seriously, they are less likely to enforce monitoring activities, such as regular reconciliations or surprise audits. This increases the opportunity for fraud to occur and remain undetected.
The Consequences of Asset Misappropriation
Financial standing
Asset misappropriation may not be the most expensive, but it can still significantly impact an organization’s financial standing in a significant way if you are not careful. One study from the ACFF found median loss for businesses that experience asset misappropriation is $120,000 per incident.
Reputation
While misappropriation of assets cannot always be directly attributed to a business’s actions, the public perception often fails to make this distinction. When assets are misappropriated, clients and customers frequently hold the organization accountable, regardless of where the actual fault lies. The reputational damage inflicted by such fraudulent activities can be severe and long-lasting. This loss of trust and credibility in the marketplace often translates into significant financial consequences, potentially triggering a downward spiral that affects the company’s bottom line for years to come.
Reported to Law Enforcement
While individual employees who commit fraud face legal consequences, businesses themselves can also encounter serious legal repercussions due to negligent oversight or corrupt practices. According to the ACFE (2024 Report to the Nations), a concerning statistic reveals that only 57% of fraud cases get reported to law enforcement authorities. This low reporting rate stems primarily from corporate management’s significant apprehension about potential negative publicity and reputational damage. The fear of public relations fallout often leads companies to handle fraud cases internally rather than involving law enforcement, potentially enabling fraudulent actors to continue their schemes elsewhere.
Bad Publicity
The employee the committed fraud will get in trouble, but in certain situations, business can attract legal issues of their own due to negligence or corruption. However, only 57% of cases of fraud are even given to law enforcement, mainly due to the fear of bad publicity on the side of management.]
Contact Timothy L. Miles Today About a Savara Class Action Lawsuit
If you suffered substantial losses and wish to serve as lead plaintiff of the Savara class action lawsuit, or just have general questions about you rights as a shareholder, please contact attorney Timothy L. Miles of the Law Offices of Timothy L. Miles, at no cost, by calling 855/846-6529 or via e-mail at [email protected]. (24/7/365).
Timothy L. Miles, Esq.
Law Offices of Timothy L. Miles
Tapestry at Brentwood Town Center
300 Centerview Dr. #247
Mailbox #1091
Brentwood,TN 37027
Phone: (855) Tim-MLaw (855-846-6529)
Email: [email protected]
Website: www.classactionlawyertn.comFacebook Linkedin Pinterest youtube
Visit Our Extensive Investor Hub: Learning for Informed Investors






